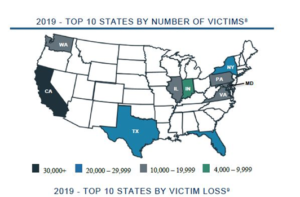
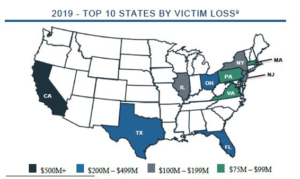
Business Email Compromise (BEC)
In 2019, the IC3 received 23,775 Business Email Compromise (BEC) / Email Account Compromise (EAC) complaints with adjusted losses of over $1.7 billion. BEC/EAC is a sophisticated scam targeting both businesses and individuals performing a transfer of funds. The scam is frequently carried out when a subject compromises legitimate business e-mail accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.
BEC/EAC is constantly evolving as scammers become more sophisticated. In 2013, BEC/EAC scams routinely began with the hacking or spoofing of the email accounts of chief executive officers or chief financial officers, and fraudulent emails were sent requesting wire payments be sent to fraudulent locations. Over the years, the scam evolved to include compromise of personal emails, compromise of vendor emails, spoofed lawyer email accounts, requests for W-2 information, the targeting of the real estate sector, and fraudulent requests for large amounts of gift cards.
In 2019, the IC3 observed an increase in the number of BEC/EAC complaints related to the diversion of payroll funds. In this type of scheme, a company’s human resources or payroll department receives an email appearing to be from an employee requesting to update their direct deposit information for the current pay period. The new direct deposit information generally routes to a pre-paid card account.
IC3 Recovery Asset Team
The Recovery Asset Team (RAT) was established in February 2018 to streamline communication with financial institutions and assist FBI field offices with the recovery of funds for victims who made transfers to domestic accounts under fraudulent pretenses.
RAT Process
The RAT functions as a liaison between law enforcement and financial institutions as they conduct statistical and investigative analysis.
Goals of RAT-Financial Institution Partnership
- Assist in the identification of potentially fraudulent accounts across the sector.
- Remain at the forefront of emerging trends among financial fraud schemes.
- Foster a symbiotic relationship in which information is appropriately shared.
Guidance for BEC Victims
- Contact the originating financial institution as soon as fraud is recognized to request a recall or reversal as well as a Hold Harmless Letter or Letter of Indemnity.
- File a detailed complaint with www.ic3.gov. It is vital the complaint contain all required data in provided fields, including banking information.
- Visit www.ic3.gov for updated PSAs regarding BEC trends as well as other fraud schemes targeting specific populations (real estate, pre-paid cards, W-2, etc.).
- Never make any payment changes without verifying with the intended recipient; verify email addresses are accurate when checking mail on a cell phone or other mobile device.
RAT Successes
The IC3 RAT has proven to be a valuable resource for field offices and victims. The following are three examples of the RAT’s successful contributions to investigative and recovery efforts.
Dallas
In December 2019, the Dallas Field Office reached out to RAT for assistance on a transfer for a $190,000 BEC incident where the victim wired funds on two separate occasions for invoice payments. The IC3 RAT’s quick action, in conjunction with the alliance built with key financial partners, led to the successful recovery of funds. This collaboration between IC3 RAT and their financial partners resulted in the exchange of key information that allowed the IC3 RAT to work in conjunction with the FBI field office to refer the case to local law enforcement. As a result, federal and local law enforcement worked together to ultimately pursue the case, which led to successful prosecution of the perpetrator.
Los Angeles
In November 2019, the IC3 RAT was asked by the Los Angeles Field Office to provide an analytical report that concentrated on elderly victims who fell victim to a variety of scams, including BEC and Romance scams, resulting in the victims transferring funds to possible money mules located in the Los Angeles area of responsibility. The IC3 RAT provided an analytical report that consisted of 19 IC3 complaints and a total loss of over $866,000. As a result of the research and analysis done by the IC3 RAT, the Los Angeles Field Office was able to conduct multiple interviews and disseminate cease and desist letters to the money mules identified.
Fort Lauderdale
In February 2019, the IC3 RAT received a complaint involving a BEC incident for $138,000, where the victim received a spoofed email and wired funds to a fraudulent bank account in Florida. The RAT took quick action and worked with key financial partners to freeze the funds. When the perpetrator attempted to withdraw funds, the RAT’s collaboration with financial partners enabled the bank employee to request the perpetrator provide documents to support the receipt of the wire. When the account holder was unable to provide legitimate documentation, the bank alerted local law enforcement and as a result, the account holder was arrested by the Fort Lauderdale Police Department.
Elder Fraud
The Elder Abuse Prevention and Prosecution Act was signed into law in October 2017 to prevent elder abuse and exploitation and improve the justice system’s response to victims in elder abuse and exploitation cases. As a response to the increasing prevalence of crimes against the elderly, especially Elder Fraud, the Department of Justice and the FBI partnered to create the Elder Justice Initiative. Elder Fraud is defined as a financial fraud scheme which targets or disproportionately affects people over the age of 60. The FBI, including IC3, has worked tirelessly to educate this population on how to take steps to protect themselves from being victimized. In 2019, the IC3 released PSAs to educate the public about Romance Fraud, common Elder Fraud schemes, and money mule activity. The FBI has held hundreds of outreach events in order to educate the public about Elder Fraud.
The Department of Justice Consumer Protection Branch (DOJ-CPB) and the FBI have also partnered to pursue fraudsters and facilitators of schemes who target the elderly. In March 2019, the FBI and other federal law enforcement partners undertook an Elder Fraud and Tech Support Fraud sweep, targeting over 260 defendants who had allegedly defrauded over 2 million U.S. victims of more than $750 million. DOJ-CPB and the FBI also target money mules who serve as the witting or unwitting facilitators of laundering proceeds from Elder Fraud schemes.
In 2019, the IC3 received 68,013 complaints from victims over the age of 60 with adjusted losses in excess of $835 million. Age is not a required reporting field. These statistics reflect only those complaints in which the victim voluntarily provided their age range as “OVER 60.” Victims over the age of 60 are targeted by perpetrators because they are believed to have significant financial resources.
Victims over the age of 60 may encounter scams including Advance Fee Schemes, Investment Fraud Schemes, Romance Scams, Tech Support Scams, Grandparent Scams, Government Impersonation Scams, Sweepstakes/Charity/Lottery Scams, Home Repair Scams, TV/Radio Scams, and Family/Caregiver Scams. If the perpetrators are successful after initial contact, they will often continue to victimize these individuals.
Tech Support Fraud
Tech Support Fraud continues to be a growing problem. This scheme involves a criminal claiming to provide customer, security, or technical support or service in an effort to defraud unwitting individuals. Criminals may pose as support or service representatives offering to resolve such issues as a compromised e-mail or bank account, a virus on a computer, or a software license renewal. Some recent complaints involve criminals posing as customer support for well-known travel industry companies, financial institutions, or virtual currency exchanges.
In 2019, the IC3 received 13,633 complaints related to Tech Support Fraud from victims in 48 countries. The losses amounted to over $54 million, which represents a 40 percent increase in losses from 2018. The majority of victims reported to be over 60 years of age. Investigative efforts have yielded many successes, including the two examples below:
Charlotte
A North Carolina man pleaded guilty to conspiracy to access a protected computer, for his role in an international tech support scam that defrauded hundreds of victims, including seniors, of more than $3 million. The subject was part of a conspiracy that carried out the scam by placing fake pop-up ads on victims’ computers to convince them they had a serious computer problem, and to induce them to pay for purported “technical support” services to resolve the issue. The IC3 provided ongoing assistance to the Charlotte Field Office and the prosecuting attorneys in this case.
Philadelphia
A Pennsylvania man pleaded guilty to wire fraud and was sentenced to 15 months imprisonment to be followed by two years of supervised release. The subject admitted to perpetrating a computer-based fraud scheme that targeted victims across the United States. As part of the scheme, the subject and others pretended to work for technology companies and contacted victims through computer pop-ups and telephone calls. Once contact was made, the subject and others induced victims to authorize payments under false pretenses and utilized remote desktop access applications to initiate unauthorized financial transactions from the victims’ financial accounts. The IC3 provided ongoing assistance to the Philadelphia Field Office for this case.
Ransomware
Ransomware is a form of malware targeting both human and technical weaknesses in an effort to make critical data and/or systems inaccessible. Ransomware is delivered through various vectors, including Remote Desktop Protocol, which allows computers to connect to each other across a network, and phishing.
In one scenario, spear phishing emails are sent to end users that result in the rapid encryption of sensitive files on a corporate network. When the victim organization determines it is no longer able to access its data, the cyber actor demands the payment of a ransom, typically in virtual currency. The actor will purportedly provide an avenue to the victim to regain access to its data once the ransom is paid.
Recent iterations of this threat target specific organizations and their employees, making awareness and training a critical preventative measure.
The FBI advises not to pay the ransom to the adversary. Paying a ransom does not guarantee an organization will regain access to its data; in fact, some individuals or organizations were never provided with decryption keys after having paid a ransom. Paying a ransom emboldens the adversary to target other organizations for profit, and provides a lucrative environment for other criminals. While the FBI does not support paying a ransom, there is an understanding that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers.
The decision to pay the ransom should not dissuade someone from contacting the FBI. In all cases the FBI encourages organizations to contact a local FBI field office immediately to report a ransomware event and request assistance.
In 2019, the IC3 received 2,047 complaints identified as ransomware with adjusted losses of over $8.9 million.